VERITI AND RAPID7
Proactively monitor and remediate risk, vulnerabilities, and misconfigurations from the OS-level and up without disrupting business.
EXECUTIVE SUMMARY
The integration of Veriti with Rapid7 InsightVM revolutionizes vulnerability assessment (VA) by enabling active vulnerability remediation. This integration leverages the compensating security controls to remediate vulnerabilities, significantly lowering attack risks without impacting business operations. It uniquely correlates vulnerabilities with security controls configuration analysis, from the OS level to the network level, enabling precise configuration changes, thereby reducing exposure risks to zero. Additionally, the solution identifies, and initiates scans on previously undetected assets, followed by a comprehensive analysis for potential remediation strategies. Post-vulnerability remediation, Veriti facilitates a full patch workflow, ensuring robust, end-to-end vulnerability management.
Solution Benefits
- Active Vulnerability Remediation
- Minimal Business Impact
- OS-Level Risk Reduction
- Comprehensive Asset Coverage
- Streamlined Patch Workflow
A PROACTIVE APPROACH WITH VERITI AND RAPID7 INSIGHTVM
Organizations grapple with the escalating complexity and volume of cyber threats. Vulnerabilities are rapidly proliferating, outpacing traditional security measures and exposing businesses to heightened risk. These vulnerabilities, often widespread and hidden, challenge organizations to maintain continuous operational functionality while addressing potential security gaps. The balancing act between effective vulnerability management and remediation in conjunction with minimal business disruption remains a crucial yet intricate endeavor.
Furthermore, the task of identifying and mitigating these vulnerabilities is resource-intensive, demanding significant time and expertise. Many organizations find themselves caught in a reactive cycle, addressing security breaches post-incident rather than proactively. This approach not only elevates the risk of successful attacks but also incurs substantial long-term costs and operational strain, emphasizing the need for a more integrated, efficient cybersecurity strategy.
Veriti, together with Rapid7 InsightVM, presents a formidable solution to these challenges. This synergy harnesses advanced analytics and comprehensive vulnerability data to enable proactive, real-time security measures. It streamlines the identification and remediation of vulnerabilities across an organization’s infrastructure, ensuring thorough coverage and minimizing operational disruptions. The integration optimizes existing security controls, automates patch workflows, and tailors defense strategies to specific vulnerabilities, thereby transforming the reactive security model into a proactive, resilient, and efficient framework, significantly reducing the risk and impact of potential cyber threats.
STRATEGIC ADVANTAGES SIMPLIFIED
By harnessing the power of AI and security configurations analytics from Veriti, coupled with the precise vulnerability data from Rapid7 InsightVM, Veriti can perform the remediations needed in one click, verifying that the changes will not impact business. This integration streamlines cybersecurity processes, significantly reducing the time and effort required for vulnerability management.
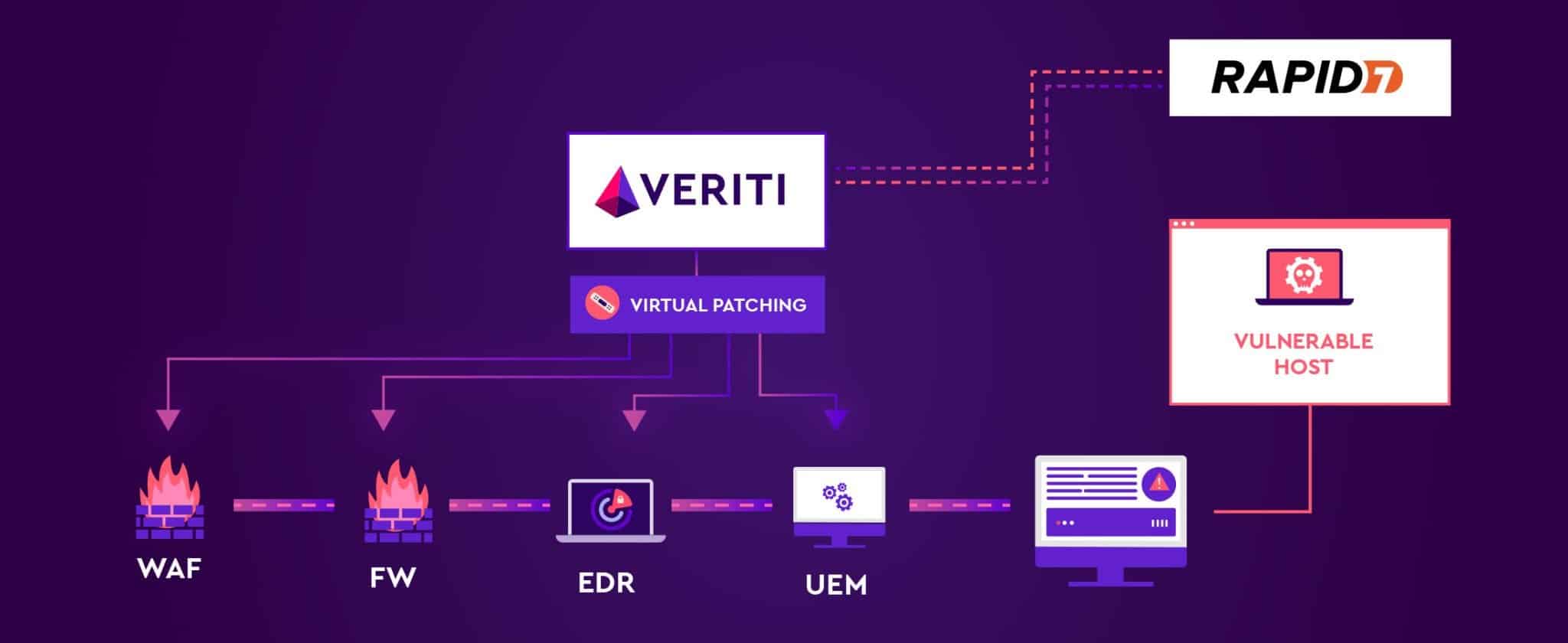
KEY FEATURES
Comprehensive Visibility into all security gaps and exposures across the security infrastructure.
Actionable Insights within Minutes by continuously analyzing your security controls, Veriti provides data-driven insights that simplify investigations and reduces MTTR dramatically
Optimize Resources – Maximize security efficiency with automated assessment and advanced security controls optimization capabilities.
One Click Remediation without Business Disruption – Identify the root cause, filter out false positives and automatically mitigate risk with confidence as every change is verified to not cause business disruption.
JOINT USE CASES
Enhanced Vulnerability Remediation Utilizing the existing security infrastructure, this integration actively remediates vulnerabilities through virtual patching of the different security tools. It minimizes attack risks by addressing vulnerabilities before they can be exploited, enhancing overall security without adding new tools or layers to the existing security stack.
OS-Level Configuration Optimization By correlating active vulnerabilities with the operating system’s state, the solution enables targeted configuration changes at the OS level. This approach significantly lowers the risk associated with exposed vulnerabilities, reducing it to zero, thus bolstering the security posture with minimal operational impact
Comprehensive Vulnerability Management This integration extends security scanning to exposed assets, not typically covered, followed by an automated analysis of potential remediation strategies. Post-analysis, it implements a full patch workflow, encompassing both virtual and OS patching, ensuring a thorough and efficient resolution of identified vulnerabilities.




