UNIFIED EXPOSURE MANAGEMENT AND REMEDIATION FOR CAASM
Combining Veriti’s Exposure Assessment and Remediation with Axonius for Proactive, Real-Time Risk Reduction
EXECUTIVE SUMMARY
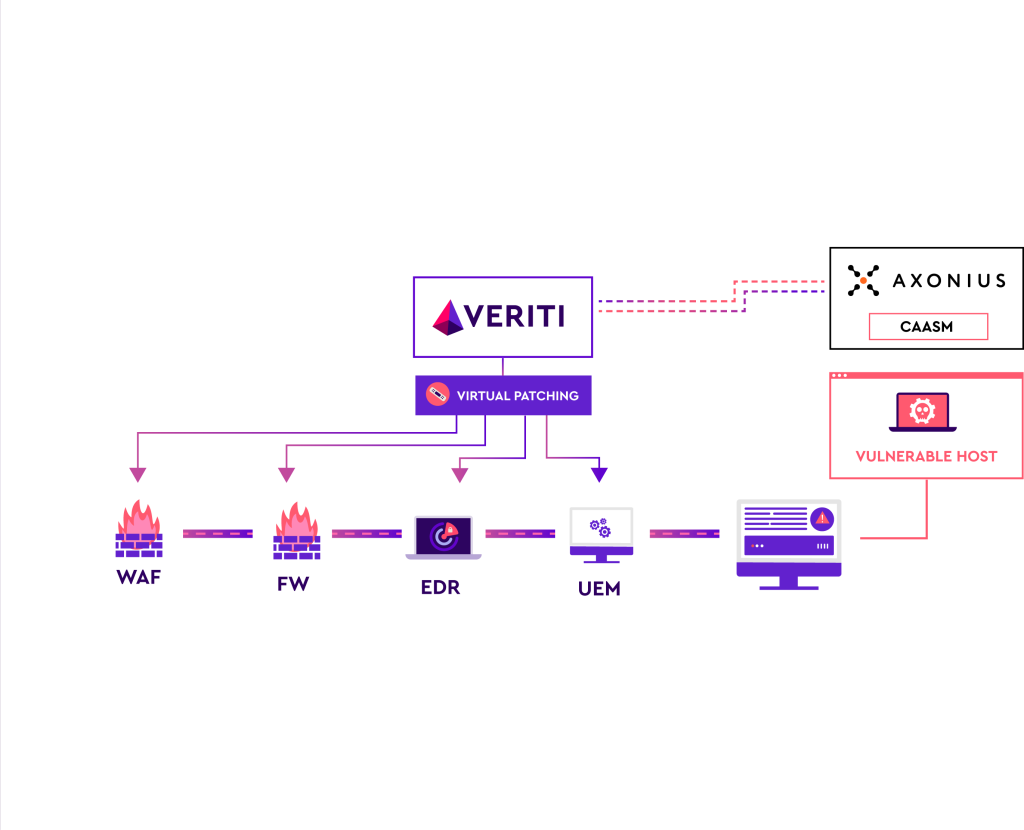
The integration between Veriti and Axonius offers a comprehensive solution that combines Veriti’s expertise in proactive exposure assessment and remediation with Axonius’s observed vulnerabilities and assets data. By integrating Veriti’s ability to identify, prioritize, and remediate misconfigurations and security gaps with Axonius’s CAASM, organizations can efficiently mitigate risks across the entire attack surface in real time.
Take Action on Axonius Findings
The integration between Veriti Exposure Assessment and Remediation and Axonius leverages Veriti’s ability to identify and remediate misconfigurations and security gaps and incorporate Axonius’s detailed analysis into actionable insights. By correlating Veriti’s deep security configuration data from various stacks, such as OS, EDR, NGFW, WAF, and more with Axonius’s Cyber Asset Attack Surface Management, organizations can proactively manage and remediate risks efficiently and in real time.
Together, Veriti and Axonius facilitate a unified approach to securing the cyber asset attack surface, providing a streamlined, effective method for enhancing organizations’ security posture. This collaboration not only identifies potential vulnerabilities but also ensures that remedial actions are comprehensive and contextually appropriate, creating a streamlined and safe method to enhance overall security posture in environments where reliability and uptime are paramount.
Key Features
Actionable Safe Remediation: Safely remediate identified risks while ensuring business continuity.
Continuous Security Control Identification: Maps all protective measures tied to assets across the entire security stack and asset attack surface.
Real Time Configuration Insights: Provides in-depth misconfiguration data for OS, EDR, NGFW, WAF, SASE, and vulnerability management systems. .
Exposure and Asset Mapping: Direct correlation of security control capabilities with identified exposures and vulnerabilities on the assets, providing a clear pathway to targeted remediation.
Network Topology Context: Insight into the network topology, detailing the protective relationships and hierarchies.
Security Event Data: Comprehensive logs of attacks and false-positive incidents associated with the asset across all implemented security controls.