Definition
Exposure assessment refers to the continuous process of identifying, evaluating, and prioritizing vulnerabilities, misconfigurations, and security gaps across hybrid environments, including on-prem, cloud, and SaaS applications. Effective exposure assessment goes beyond simple vulnerability scanning to assess security control effectiveness, map compensating controls, and identify gaps in real time protection. By correlating asset data, configuration drift, threat intelligence, and real-world exploitability, exposure assessment helps organizations proactively manage risk and continuously improve their security posture.
Purpose of Exposure Assessment:
- Risk Identification: To systematically identify security vulnerabilities that could be exploited by threat actors.
- Risk Analysis: To evaluate the potential impact and likelihood of these vulnerabilities being exploited.
- Prioritization of Risks: To help organizations prioritize their security efforts based on the severity and potential impact of identified exposures.
- Assess Security Controls: Identify misconfigurations, compensating controls, and policy drift across the entire security stack, including EDR, NGFW, WAF, and CNAPP.
- Identify Business Impact: Evaluate how exposures affect business-critical assets, aligning security actions with operational priorities and potential business disruptions.
- Enhance Threat Correlation: Link exposures to real-world threat intelligence, including active attack campaigns, MITRE TTPs, and Indicators of Compromise (IoCs).
Key Components of Exposure Assessment:
- Continuous Security Control Assessments: Monitor and assess security configurations across firewalls, EDR, WAF, CNAPP, VA, and more — ensuring configurations align with best practices and real-time threat intelligence.
- Comprehensive Data Aggregation: Ingest, normalize, and deduplicate data from vulnerability scanners, BAS tools, CNAPPs, EASM, and asset management platforms, creating a unified view of exposures.
- Threat Intelligence Correlation: Map each exposure to live threat intelligence, tracking active exploitations, associated threat actors, and known attack chains to prioritize risk based on real-world threats.
- Prioritized Exposure Scoring: Combine CVSS, EPSS, and Veriti’s own Vulnerability Prioritization Score (VPS), which factors in asset criticality, compensating controls, exploitability, and business context.
- Business Context Mapping: Enrich exposure data with business asset information, identifying exposures on critical systems and correlating risk directly to operational impact.
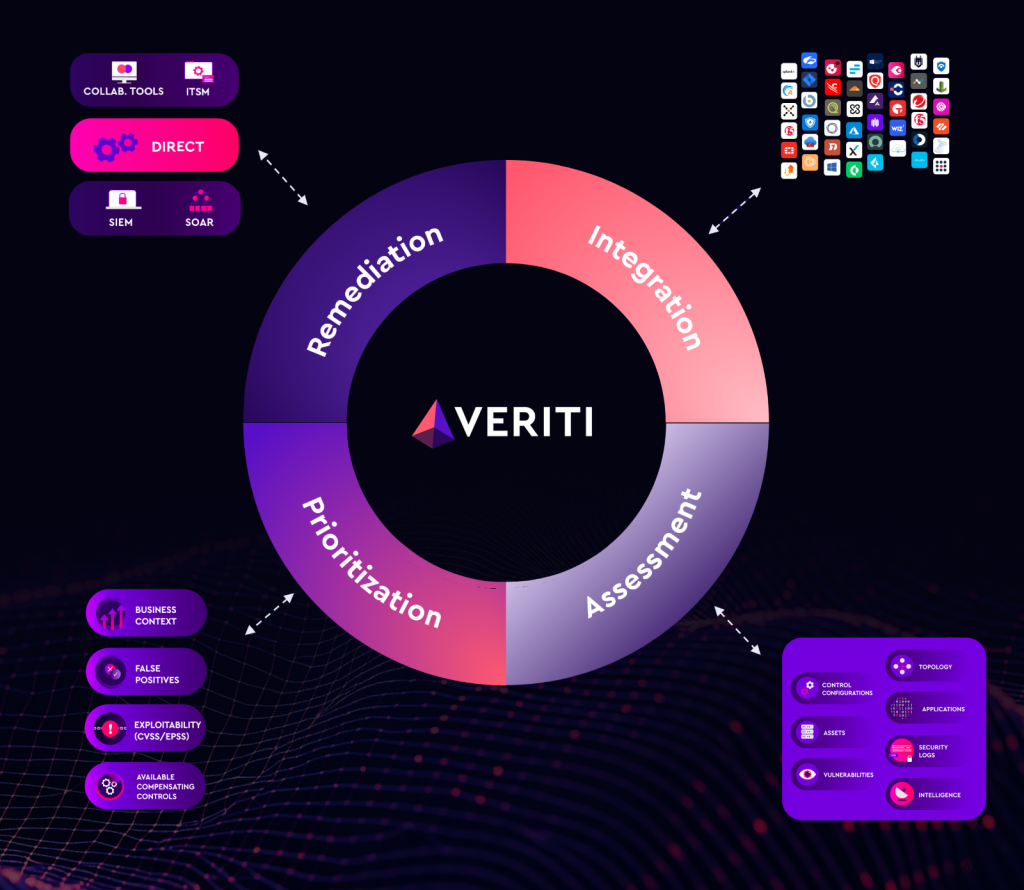
How Veriti Enhances Exposure Assessments
Veriti enhances traditional exposure assessments by combining comprehensive visibility, advanced prioritization, and safe, automated remediation across the entire security stack. Through continuous integration with over 70 security tools, Veriti aggregates, normalizes, and deduplicates exposure data from all sources, providing a single source of truth for security and risk teams. Its advanced prioritization engine incorporates threat intelligence, compensating control effectiveness, and business context to ensure remediation efforts focus on exposures with the highest potential impact. By enabling one-click remediation directly from the assessment platform, Veriti closes the loop between assessment and action, reducing risk faster and more efficiently — without disrupting business operations.
Strategies for Effective Exposure Assessment:
- Continuous Monitoring: Implementing tools and processes for continuous monitoring of the network to detect and respond to vulnerabilities promptly.
- Integration of Security Practices: Integrating exposure assessment with overall security practices like patch management, incident response, and security training.
- Stakeholder Involvement: Engaging stakeholders from various departments to ensure a comprehensive understanding of all potential risks.
- Centralized Exposure Management: Leverage a single platform to unify exposure data across all security tools and environments, ensuring complete, contextual visibility.
- Compensating Control Validation: Identify which exposures are mitigated by existing security controls, reducing redundant remediation and focusing resources on unprotected risks.
- Automated Prioritization: Use a combination of business impact analysis, compensating control validation, and real-world exploitability to dynamically prioritize remediation efforts.
- Cross-Platform Remediation: Mobilize remediation across EDR, WAF, NGFW, cloud, and endpoints directly from the exposure assessment platform — with full auditability and business impact validation.
Benefits of Conducting Exposure Assessments:
- Unified Visibility Across Environments: See exposures across on-prem, cloud, and SaaS environments in a single platform — eliminating blind spots and security silos.
- Prioritized Remediation: Focus efforts on exposures with the highest real-world risk, validated by threat intelligence, exploitability data, and compensating control effectiveness.
- Continuous Risk Reduction: Proactively identify and close security gaps before they are exploited, maintaining continuous protection across your evolving attack surface.
- Measurable Operational Impact: Track labor saved, MTTR reduction, and cost savings from automated remediation actions, proving the value of your exposure management program.
- Improved Security Posture: Continuously measure and improve your overall security posture through automated exposure assessments and integrated remediation workflows.
Best Practices for Conducting Exposure Assessments:
- Regular Assessments: Conducting exposure assessments regularly to account for new threats and changes in the IT environment.
- Use of Advanced Tools: Leveraging advanced vulnerability scanning and penetration testing tools that can simulate the latest attack techniques.
- Training and Awareness: Training security teams to recognize and respond to new vulnerabilities and exposures as part of a continuous learning process.
- Leverage Existing Tools: Maximize the value of your existing security investments by integrating exposure assessment with EDR, NGFW, WAF, and vulnerability management tools.
- Real Time Threat Intelligence: Continuously enrich exposure data with live threat intelligence to understand how attackers are actively exploiting vulnerabilities in the wild.
- Track Business Impact: Align exposure prioritization with business-critical assets, ensuring remediation actions directly support operational resilience and regulatory compliance.
- Automate Safe Remediation: Mobilize one-click remediation actions directly from the exposure assessment platform, reducing MTTR and ensuring no business disruption.
Exposure assessment is a vital component of an organization’s cyber security strategy. It provides essential insights into vulnerabilities and potential threats, enabling organizations to manage their risk effectively. Regularly conducting exposure assessments helps maintain a robust defense against cyber threats and supports compliance with regulatory requirements.




