Veriti Research has uncovered a potentially growing cyber threat campaign surrounding the release of the declassified JFK, RFK, and MLK files. Attackers are capitalizing on public interest in these historical documents to launch potential malware campaigns, phishing schemes, and exploit attempts. Our research indicates that cybercriminals are quick to react to major public events, and this case is no exception.
As the files gain media attention, attackers are starting to create potential infrastructure for their upcoming attacks.
The Fast Response Time of Cybercriminals
Veriti Research has observed that attackers are incredibly swift in crafting scams and launching attacks following significant global events. Within days of the announcement regarding the declassification of JFK-related files, several suspicious domains were registered, seemingly designed to impersonate legitimate sources.
Some of the domains identified include:
- Thejfkfiles[.]com – Registered on January 23
- jfk-files[.]com – Registered on January 23
- rfkfiles[.]com – Registered on January 24
- jfk-files[.]org – Registered on January 25
These domains raise red flags as they could be leveraged for malicious activities, such as phishing attacks, malware distribution, or social engineering tactics to steal credentials.
Key Attack Vectors Identified
Based on Veriti Research findings and past research on similar events, cybercriminals are and will use multiple attack techniques to take advantage of users seeking access to the declassified files:
- Malware-Laced Files: Attackers are embedding malware into files labeled as “official” JFK document releases. Unsuspecting users who download these files may unknowingly infect their devices with spyware, ransomware, or trojans.
- Fake Phishing Websites: Fraudulent websites mimicking official sources lure users into downloading harmful files or entering sensitive information. These phishing pages may appear convincing, using similar branding and layouts as government or media sites.
- Embedded Exploits in Browsers: Some malicious websites exploit browser vulnerabilities as soon as a user visits them. By using zero day vulnerabilities or known exploits, attackers can execute remote code and compromise the visitor’s system.
- Email-Based Phishing Attacks: Cybercriminals are sending phishing emails posing as journalists, historians, or official institutions offering “exclusive” access to newly released JFK files. These emails often contain malicious attachments or links leading to infected downloads.
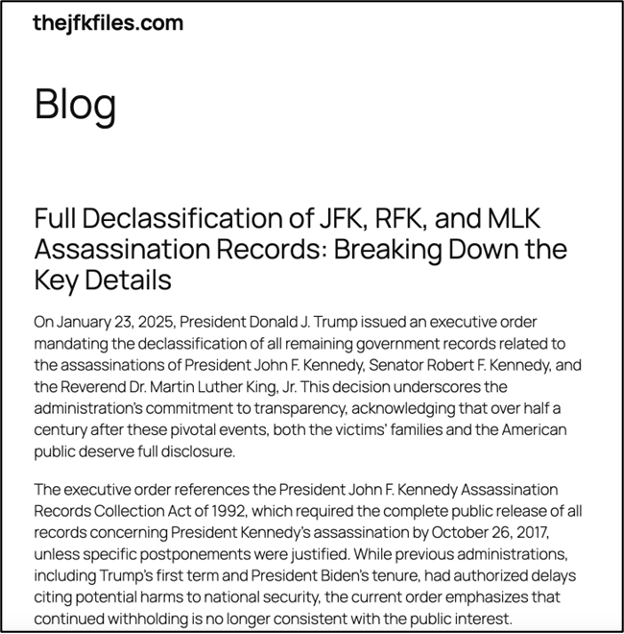
**although the above site might be legit for now, it might be a way to build reputation for a ‘day of an attack’
The Bigger Cybersecurity Picture
Events of historical and public significance have always been prime opportunities for attackers. Similar trends have been observed with past global events, including COVID-19 scams, election related campaigns, and cryptocurrency frauds.
The upcoming attacks leveraging the JFK files highlight the importance of cyber resilience in the face of social engineering tactics. Threat actors know that urgency and curiosity often lead to reduced vigilance, making individuals and organizations vulnerable to scams. This is why verifying sources before downloading files is critical. Only access declassified JFK files from official government websites such as the National Archives or other well known sources. Avoid downloading files from unknown third party websites or social media links, as attackers often disguise malicious content under seemingly legitimate branding. As always, if something looks suspicious, it’s best to avoid clicking links or downloading attachments.
The exploitation of the JFK files is just another example of how quickly cybercriminals can adapt to real world events.
Veriti Research will continue monitoring developments around these cyber threats and provide updates as new attack methods emerge. Stay informed, stay cautious, and help others stay protected by sharing cybersecurity awareness within your organization and network.




