Attackers are actively targeting OpenAI, exploiting CVE-2024-27564, a Server-Side Request Forgery (SSRF) vulnerability in commit f9f4bbc. Veriti’s latest research reveals that this vulnerability, despite being classified as medium severity, has already been weaponized in real world attacks.
Our research uncovers:
- Active exploitation in the wild, with over 10,479 attack attempts from a single malicious IP.
- 35% of organizations analyzed are unprotected due to misconfigurations in IPS, WAF, and firewall settings.
- Financial institutions are prime targets, as attackers seek to exploit AI-powered services and API integrations.
This research highlights a crucial takeaway: No vulnerability is too small to matter, attackers will exploit any weakness they can find.
The Threat: CVE-2024-27564 in Action
CVE-2024-27564 is a server-side request forgery (SSRF) vulnerability in commit f9f4bbc. It allows attackers to inject malicious URLs into input parameters, forcing the application to make unintended requests on their behalf.
Watch the attack in action: Attack Demo Video
Key Findings
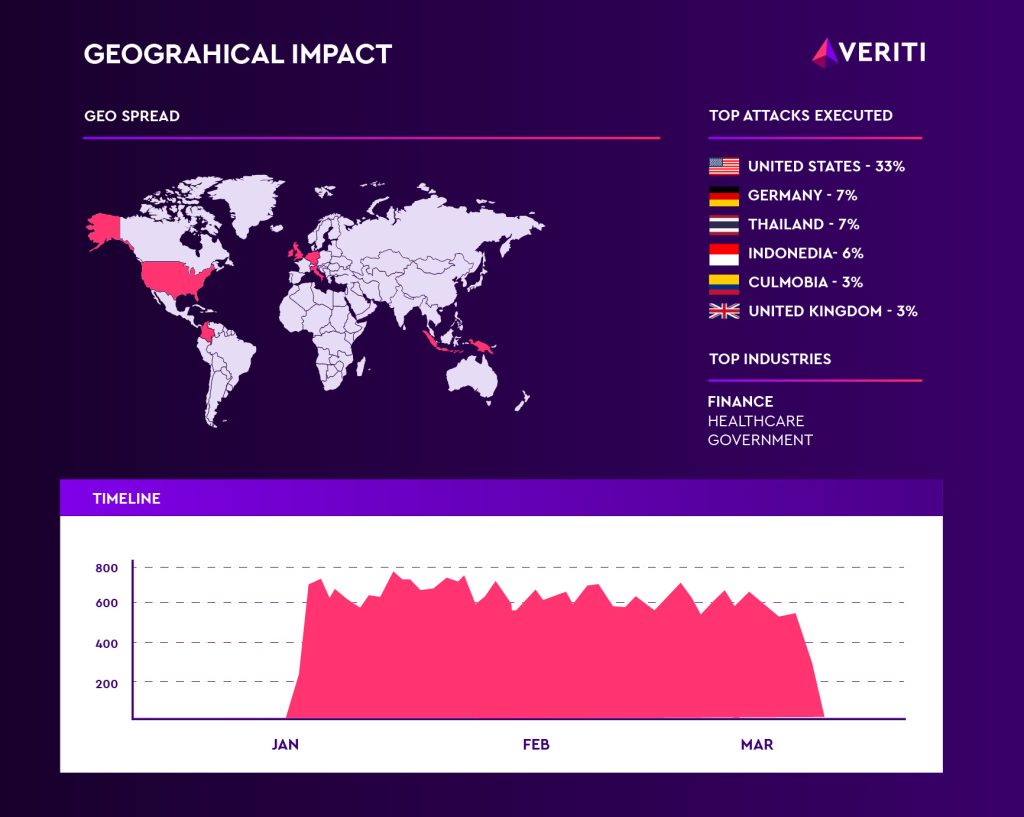
- Over 10K attack attempts in a week observed from multiple attackers.
- Top targeted industry and geo are Government organisations in the US.
- 35% of companies analyzed were unprotected due to misconfigured Intrusion Prevention Systems in their NextGenFirewall or WebApplicationFirewall
Despite its low EPSS rating, this vulnerability has already become a real-world attack vector, proving that severity scores don’t dictate actual risk.
Financial Sector: A Prime Target
Veriti’s research identifies financial institutions as top targets for attacks leveraging CVE-2024-27564. Why? Banks and fintech firms depend on AI-driven services and API integrations, making them vulnerable to SSRF attacks that access internal resources or steal sensitive data.
The risks? These attacks could lead to:
- Data breaches
- Unauthorized transactions
- Regulatory penalties
- Reputational damage
Ignoring medium-severity vulnerabilities is a costly mistake, particularly for high-value financial organizations.
Why Medium-Severity Vulnerabilities Still Pose a Risk
Security teams often prioritize patching only critical and high-severity vulnerabilities. But attackers exploit whatever works, regardless of ranking. Exploitation trends change: A once-ignored vulnerability can quickly become a favorite attack vector. Automated attacks scan for weaknesses, not severity scores, and misconfigurations create easy entry points, even well secured systems remain vulnerable when IPS or WAF rules are incorrectly set.
CVE-2024-27564 is proof that ignoring medium-severity vulnerabilities is dangerous.
Attackers Exploiting CVE-2024-27564 include:
- 31.56.56[.]156
- 38.60.191[.]7
- 94.156.177[.]106
- 159.192.123[.]190
- 119.82.255[.]34
- 103.251.223[.]127
- 104.143.229[.]115
- 114.10.44[.]40
- 116.212.150[.]192
- 145.223.59[.]188
- 167.100.106[.]99
- 174.138.27[.]119
- 212.237.124[.]38
- 216.158.205[.]221
Final Thought: Remediate everything you can – because you never know where the next attack will come from.
Next Steps for Security Teams
Check your IPS, WAF, and Firewall configurations for protection against CVE-2024-27564.
Monitor logs for attack attempts from known attacker IPs.
Prioritize AI-related security gaps in risk assessments.
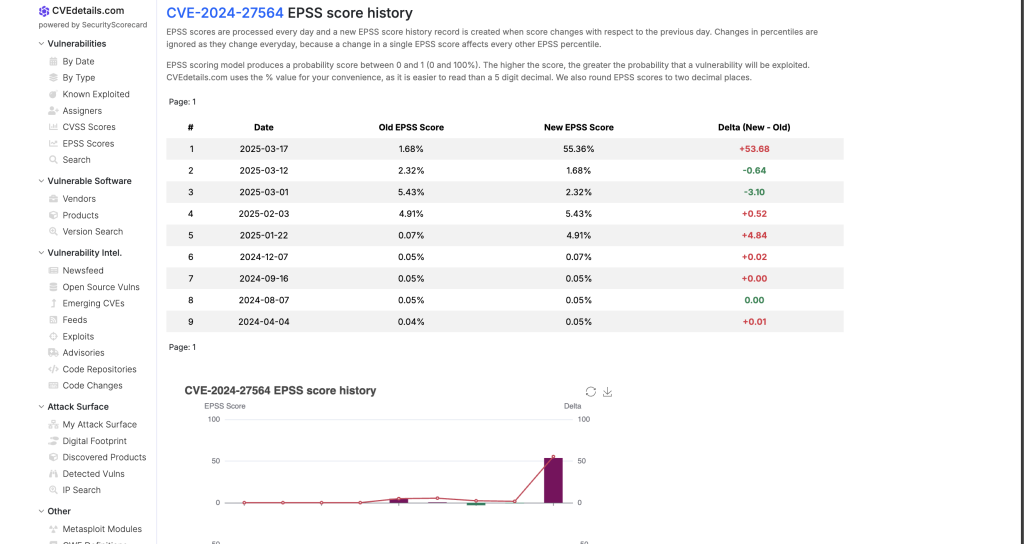
Update March 20th
CVEdetails.com reflects the updated EPSS score of the CVE based on the research we uncovered. It’s previous score was 1.68% and now it is 55.36%