It is a never-ending race and the odds are stacked against us. There are just too many vulnerabilities lurking in our environment. There are too many vulnerabilities that pose significant risks to the organization. The statistics speak volumes: each year witnesses a substantial growth in the number of vulnerabilities discovered. This amplifies the urgency for organizations to strengthen their defenses.
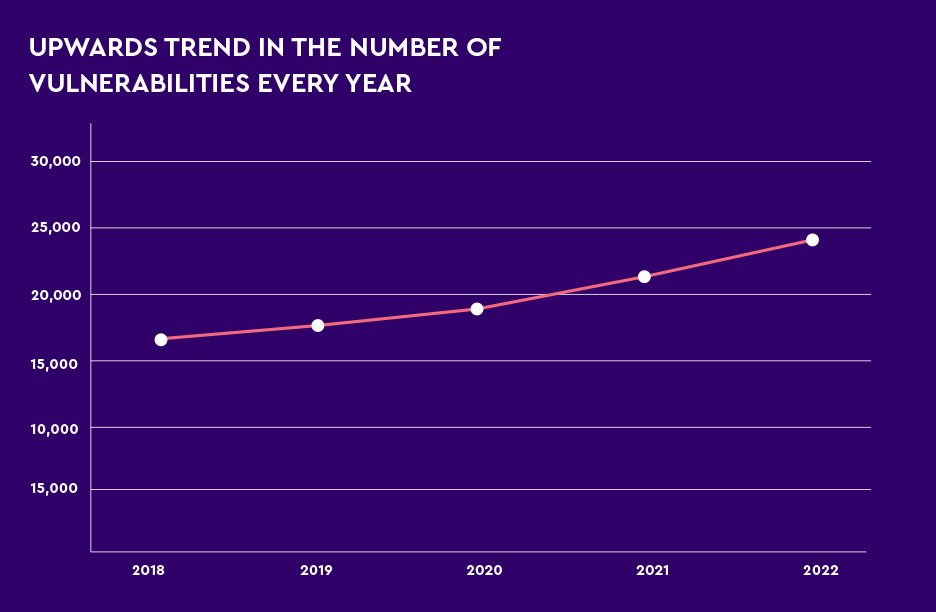
It is crucial to address these vulnerabilities swiftly and efficiently, considering the substantial time it takes to mitigate a single vulnerability, let alone remediate a critical one. To navigate this challenging landscape, organizations must adopt best practices and unleash the art of vulnerability mitigation. This is essential for safeguarding their digital assets effectively, all without disrupting business operations whatsoever.
EMBRACE A PROACTIVE AND DYNAMIC DEFENSE STRATEGY
With vulnerabilities multiplying at an alarming rate, organizations must adopt a proactive mindset to combat potential risks. Staying ahead of threats requires continuous monitoring of the security configurations of all different defense layers deployed in the organization. All configurations should be correlated with vulnerability assessment and breach and Attack Simulation (BAS) reports. By proactively identifying where the security gaps and misconfigurations are and promptly responding to potential risks, organizations can mitigate vulnerabilities before attackers exploit them. It is essential to foster a culture of cybersecurity awareness and responsibility, empowering different security teams to be actively involved in this proactive effort via implementing cross- team collaboration processes.
INCORPORATE DIVERSE SECURITY LAYERS
As the number of vulnerabilities continues to surge, organizations must deploy a multi-layered defense approach to fortify their digital perimeters. This involves implementing a comprehensive range of security measures, including network, endpoint, mail, and application security solutions. By employing diverse security layers, organizations can create multiple barriers against potential attacks. Thus, minimizing the likelihood of successful breaches. Network access control solutions, intrusion prevention systems (IPS), secure email gateways (SEG) and endpoint protection products (EPP) enhance threat detection and prevention capabilities, providing a robust security posture.
IMPLEMENT VIRTUAL PATCHING AND MITIGATION CONTROLS
The time it takes to mitigate a vulnerability can significantly impact an organization’s security posture. In situations where official patches are not readily available or feasible, waiting endlessly for the next maintenance window or regulations does not allow patching, organizations must adopt virtual patching techniques. Virtual patching enables prompt vulnerability mitigation by implementing temporary security measures until patching the actual assets is again relevant. Additionally, making configuration adjustments to network and endpoint security tools further strengthens the organization’s defenses against emerging threats. Web application firewalls (WAFs) equipped with virtual patching capabilities act as proactive defense mechanisms, safeguarding organizations from potential attacks.
LEVERAGE NETWORK SEGMENTATION
Network segmentation plays a vital role in containing the impact of potential infections. By isolating critical systems and segmenting the network, organizations can limit lateral movement within their infrastructure. This approach protects systems that cannot be immediately patched or remediated and provides an additional layer of defense against unauthorized access. Combined with virtual patching, network segmentation is an effective strategy to compartmentalize just the relevant network portion and safeguard critical assets, reducing the potential impact of breaches.
MANAGE POLICY EXCEPTIONS to ensure business uptime
In some instances, organizations may face challenges in remediating or mitigating vulnerabilities due to fear of business disruptions. Security experts need to stay vigilant about the business impact hardening the security defenses might cause. Establishing clear policies to create exceptions is crucial to ensure smooth business operations. Organizations must make crucial decisions regarding which traffic, protocols, and applications to enable in all cases. This means setting procedures involving all relevant stakeholders, regularly reviewing, and assessing the effectiveness of policy exceptions.
VERITI’s unique virtual patching
Veriti enables organizations to virtually patch vulnerabilities in the different defense layers (WAF, NGFWs, and EDR) while ensuring uninterrupted business operations.
Veriti’s unique virtual patching turns vulnerability assessment, and BAS reports into practical actions. These actions are implemented by applying security updates and configuration changes at the network segment level rather than waiting endlessly to patch the unpatchable. This method effectively reduces the time and effort needed to patch individual devices, which helps minimize disruptions to patient care and maintain a secure environment.
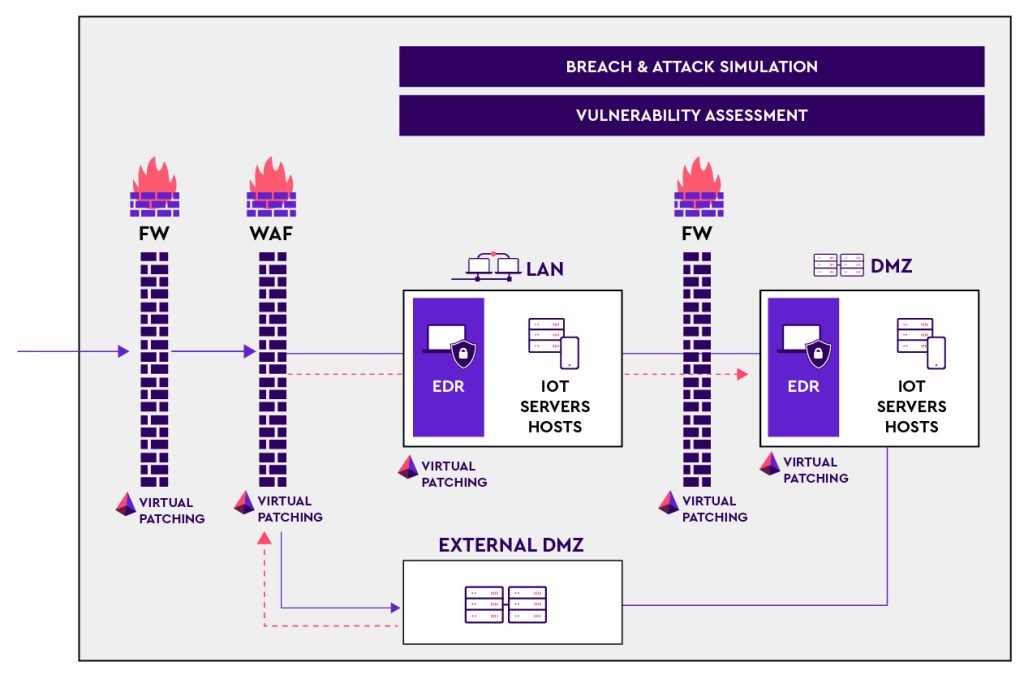
By continuously monitoring emerging threats and vulnerabilities, Veriti can proactively identify potential attack vectors and apply virtual patches to mitigate risks promptly while ensuring the required change will not affect business operations




