Veriti research recently analyzed stolen data that was published in a telegram group named “Daisy Cloud” (potentially associated with the RedLine Stealer), exposing the inner workings of a cybercrime marketplace. This group offers thousands of stolen credentials in an ongoing basis across a wide range of services, from crypto exchanges to government portals, at disturbingly accessible prices.
From our point of view, this case highlights not only the scale of credential theft, but also the continued operational maturity of infostealer ecosystems and underground data monetization.
The Marketplace for Stolen Data
On the 18th of October, 2023, a telegram group was created, exposing sensitive data potentially related RedLine Stealer. Daisy Cloud, the actor behind it, offers competitive pricing for stolen information – including access to financial platforms, cloud services, and even government portals.
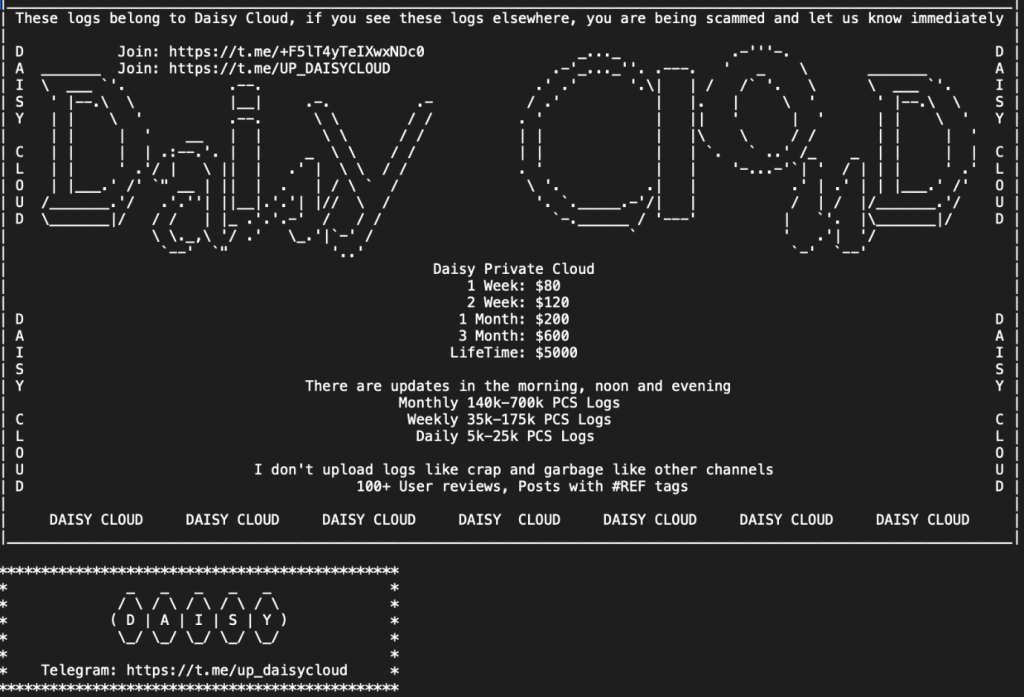
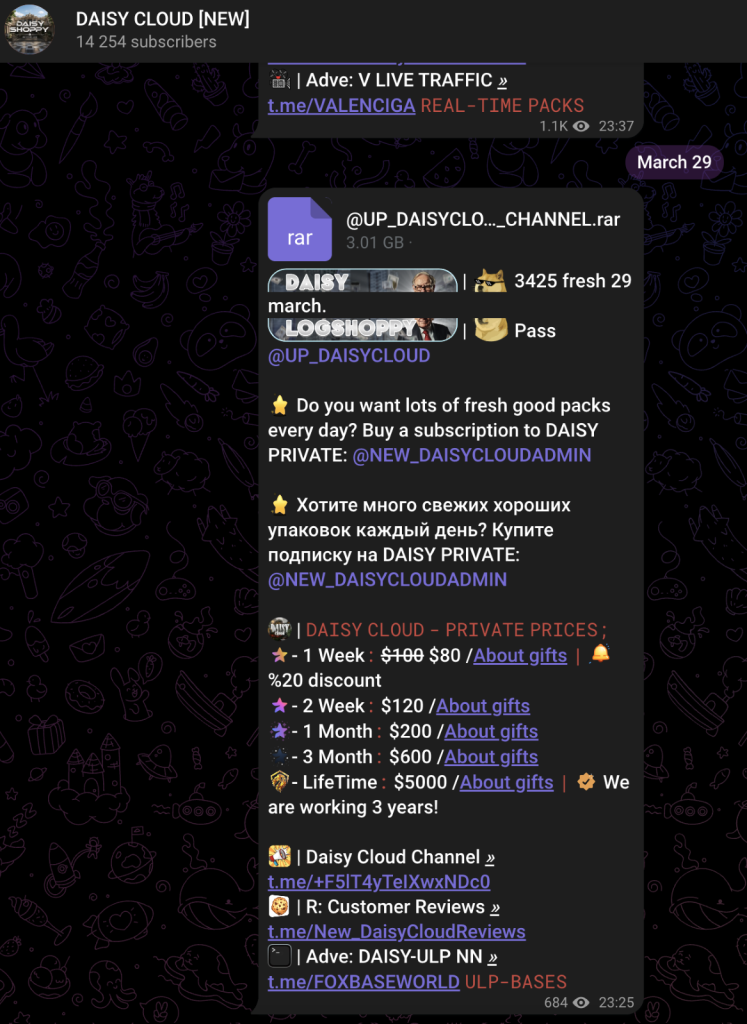
A snapshot of the marketplace interface.
A Deep Dive into the Data
The data was posted on a well-known hacker forum, providing a rare window into the scope and scale of the breach. Veriti research analyzed the dump and uncovered key statistics:
1,992 unique infected hosts
30,970 unique credentials
25,693 unique services (websites or apps tied to credentials)
108 unique countries represented (based on OS data)
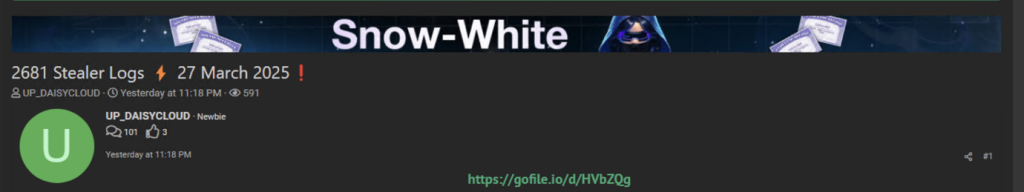
An example of listings offered by the actor.
Cryptocurrency Exposure
A notable portion of the leaked credentials targets cryptocurrency platforms, confirming that financial theft remains a top motive:
- Binance[.]com
- Coinbase[.]com
- Crypto[.]com
- Xtb[.]com
- Bitcoinhash[.]co
In addition to login credentials, the leak also includes actual Bitcoin wallet keys.
Personal Services Compromised
Veriti research also found extensive credential exposure tied to popular personal services, such as:
- Facebook[.]com
- Netflix[.]com
- Live[.]com
- Twitter[.]com
- Adobe[.]com
- tax.gov[.]ma
- disneyplus[.]com
- zoom[.]us
- x[.]com
- onlyfans[.]com
- chat.deepseek[.]com
- account.box[.]com
- amazon[.]in
- aliexpress[.]com
Government Service Credentials
The presence of government portal logins significantly raises the threat level. Among the affected domains were:
- e-albania.gov[.]al
- eservice.dpdt.gov[.]bd
- portal.incometaxindiaefiling.gov[.]in
- id.nadra.gov[.]pk
- voters.eci.gov[.]in
- login.caixa.gov[.]br
- sso.dancuquocgia.gov[.]vn
- giris.turkiye.gov[.]tr
- mca.gov[.]in
Sensitive Corporate Credentials
Enterprise cloud credentials were also included, some of which grant access to critical IT infrastructure:
- id.atlassian[.]com
- godaddy[.]com
- signin.aws.amazon[.]com
- cloud.mongodb[.]com
Geographic and OS Distribution
The data also reveals interesting geographic and system-level patterns among infected hosts.
Infections by Geographic location:
Infections by Operating System:
Server Level Exposure
As part of its deep dive into the data, The Veriti research team encountered multiple compromised cloud and on-prem servers across several countries, each revealing how deeply cybercriminals can infiltrate sensitive environments.
While we are omitting technical specifics for security reasons, we can confirm the following:
- A server in Southeast Asia, likely tied to an educational institution, was exposed with administrative privileges and no antivirus protection. The applications and configuration indicated that it was used for development purposes, making it a potential launch point for deeper attacks within the network.
- A cloud server in Northern Europe was identified with tools commonly used by DevOps professionals, including network packet analyzers and cloud automation agents. Its configuration suggests the server played a role in managing infrastructure, a high value asset if exploited.
- Another server in the Middle East was found with access to a wide range of services, including government portals, identity platforms, and financial systems. The range of applications suggested multi-user access, raising concerns over shared administrative environments within sensitive sectors.
To protect the affected organizations, Veriti is not publishing any identifying information such as host names, IP addresses, or account names.
Beyond individual endpoints, Veriti research uncovered signs of coordinated infections across full network segments. These networks, in regions including Poland, the Netherlands, the UK, Panama, the US, and Italy, each contained multiple infected systems.
This level of infiltration suggests attackers are leveraging lateral movement techniques as the initial stage of broader access operations, potentially paving the way for ransomware deployment, data exfiltration, or further credential harvesting.
The Daisy Cloud incident is a powerful reminder: credentials are not just data points, they are keys to identities, finances, and infrastructure. The exposure of 30,000+ logins across nearly every category of digital life reflects a mature and thriving cybercrime economy.
From Veriti’s perspective, proactive credential monitoring, OS-level hardening, and remediation-first security strategies are essential to staying ahead of these threats.




