Organizations don’t just need more threat intelligence – they need actionable threat intelligence that actually reduces risk before exploitation. Traditional threat intel feeds offer static, generic indicators that often fail to reflect the real time threats targeting your specific environment.
At Veriti, we believe threat intelligence should work for you, not overwhelm you.
Adaptive Threat Intelligence
Security teams are already drowning in data. Between access logs, threat feeds, alerts, and triage workflows, the challenge isn’t a lack of information, it’s identifying what matters right now.
The Adaptive Block List is purpose-built to bridge that gap:
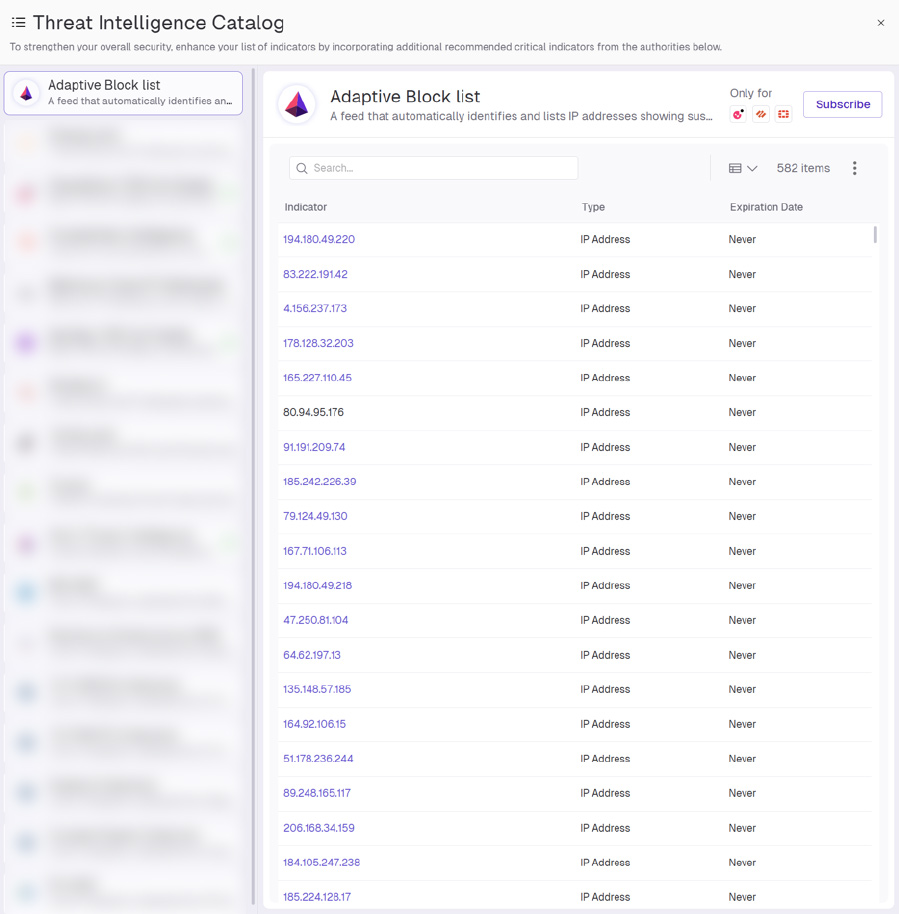
“A feed that automatically identifies and lists IP addresses showing suspicious or malicious behavior in your firewall access logs, enabling immediate blocking of potential threats.”
This is not your typical static threat feed. It adapts to your environment in real time, using behavioral signals, firewall access logs, and enrichment from reputation engines to surface indicators relevant to your actual attack surface.
By automating the extraction of IOCs and intelligently correlating behaviors, Veriti eliminates up to 80% of the manual work typically done by SOC analysts, freeing up teams to focus on what matters most.
Visual Intelligence: Blocking at Scale
The Adaptive Block List provides unmatched visibility and control, with hundreds of thousands of IPs dynamically evaluated and blocked based on real time threat behaviors. This isn’t about waiting for global feeds to catch up. This is about your environment, your exposure, your protection.
While other feeds like Shodan, CrowdStrike, or FS-ISAC deliver valuable external indicators, Veriti’s Adaptive Block List complements and amplifies them by personalizing enforcement decisions based on real time internal telemetry.
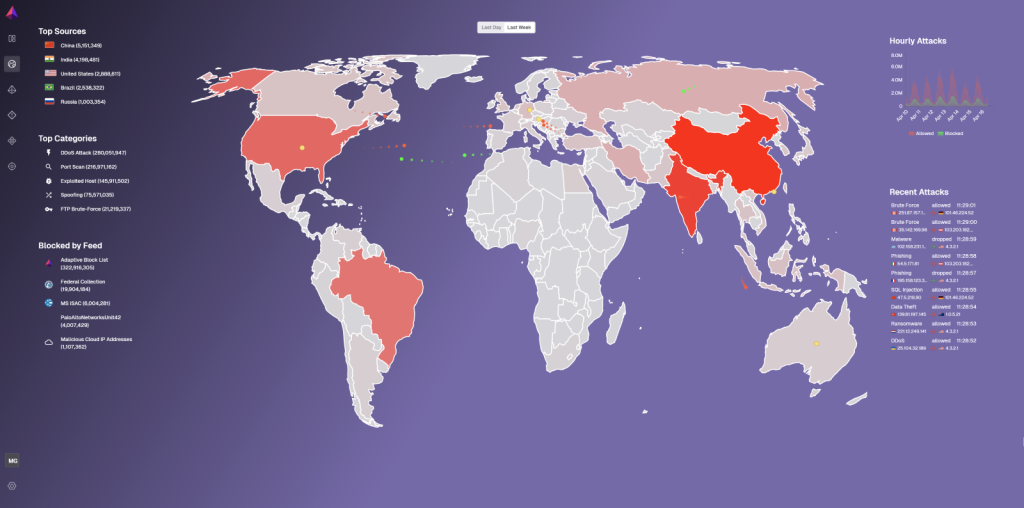
Global Threat Exposure: What We’re Blocking
This isn’t just theory. Our exposure map tells the real story. Over the last week, Veriti has blocked threats from top malicious sources including:
- China: 5.5M+ attacks
- India: 4.1M+
- United States: 2.8M+
- Brazil and Russia: 2.5M+ and 1M+ respectively
Top attack categories include:
- DDoS Attacks
- Port Scans
- Exploited Hosts
- Spoofing
- FTP Brute-Force
With over 322 million threats blocked by the Adaptive Block List feed alone, organizations are empowered to move from reactive alert chasing to proactive enforcement.
Beyond Prevention: Intelligent Access Control
Veriti doesn’t stop at blocking. Our platform goes a step further by correlating threat intelligence with known vulnerabilities in your environment, automating exposure assessments and delivering attack surface-aware recommendations.
By continuously analyzing how well your compensating controls are utilized, Veriti helps security teams optimize security controls and prioritize safe remediation.
This shifts the conversation from “Are we blocking threats?” to “Are we using our tools intelligently to reduce real risk?”
Automated Intelligence. Human Impact.
CISOs and security leaders are constantly balancing cost, complexity, and coverage. Veriti’s Adaptive Block List lightens that burden through:
- Automated IOC extraction from real time access logs
- Behavioral analysis over static threat matching
- Security stack integration for cross-stack enforcement
- Time savings and cost reduction for overburdened SOC teams
It’s not about adding more threat feeds, it’s about making threat intelligence actionable, adaptive, and aligned to your organization.
We believe that intelligent automation, like the Adaptive Block List is key to reducing the gap between detection and prevention. It’s also a critical step in elevating the role of threat intelligence from passive feed to active enforcement engine.
By turning firewall access logs into an intelligent, adaptive feed of blockable threats, Veriti empowers organizations to enforce real time protection where it counts most.
Rather than chasing alerts or drowning in IOCs, consider what it would look like if your controls knew what to block, before your team even had to ask.




