Organizations often face technical and business constraints that make it difficult to implement standard security measures. Compensating controls offer a solution by providing alternative security measures that effectively mitigate risk to an acceptable level. At Veriti, we emphasize a modern approach to improving security posture through continuous automated assessment and optimization of security controls. Our two-pronged strategy leverages the same APIs used to fetch all configurations to apply actual remediation guidelines, encompassing compensating controls from the OS-level to the cloud.
Understanding Compensating Controls
Compensating controls are security measures implemented to meet the requirements of a security standard when the primary controls cannot be directly applied. These controls are designed to offer equivalent or greater levels of protection, addressing physical, administrative, or technical limitations. The purpose of compensating controls includes:
- Risk Management: Managing and reducing risks associated with security vulnerabilities when primary controls are not feasible.
- Operational Continuity: Maintaining business operations while addressing security requirements through alternative means.
Common Scenarios for Using Compensating Controls
Legacy Systems
Upgrading or changing legacy systems to meet current security standards can be impractical or disruptive. Compensating controls offer a way to protect these systems without significant modifications.
Financial Constraints:
Budget limitations may prevent the implementation of the best security practices or technologies. Alternative measures can provide necessary security within budgetary limits.
Technical Limitations
In environments where desired security controls cannot be implemented without impairing system functionality, compensating controls provide a viable solution.
Live Threats
When persistent threats can’t wait for scheduled downtime to apply a patch, compensating controls provide a quick preventive solution.
Examples of Compensating Controls
Expired Licenses for Multiple Products
If licenses for critical security products like Anti-Virus, Anti-Bot, Intrusion Prevention System (IPS), and Threat Emulation expire, compensating controls can involve deploying enhanced monitoring and logging to detect any anomalies or threats that these tools would have typically blocked.
Addressing Disabled Anti-Virus Protections
When an Anti-Virus license expires, compensating controls might include increasing the frequency of system scans using other available security tools and implementing stricter access controls to limit the potential spread of malware.
Mitigating the Lack of Anti-Bot Protections
If the Anti-Bot license expires, organizations can deploy compensating controls such as using network segmentation to isolate critical systems and deploying application firewalls to filter out suspicious traffic.
Substituting Expired Intrusion Prevention System (IPS) Protections
When an IPS license expires, compensating controls might involve increasing the sensitivity of other detection tools and employing manual threat hunting to identify and mitigate potential intrusions.
To maximize the effectiveness of compensating controls, organizations should adopt best practices centered around Automated Security Control Assessment (ASCA). Regular automated analysis using ASCA is essential to ensure that compensating controls are functioning as intended and remain compliant with relevant standards. This ongoing assessment process helps to identify any gaps or weaknesses in the controls, allowing for timely adjustments. Additionally, ASCA facilitates continuous improvement by enabling organizations to regularly reassess and enhance their compensating controls in response to new threats and changes in the environment.
Veriti’s Approach to Compensating Controls
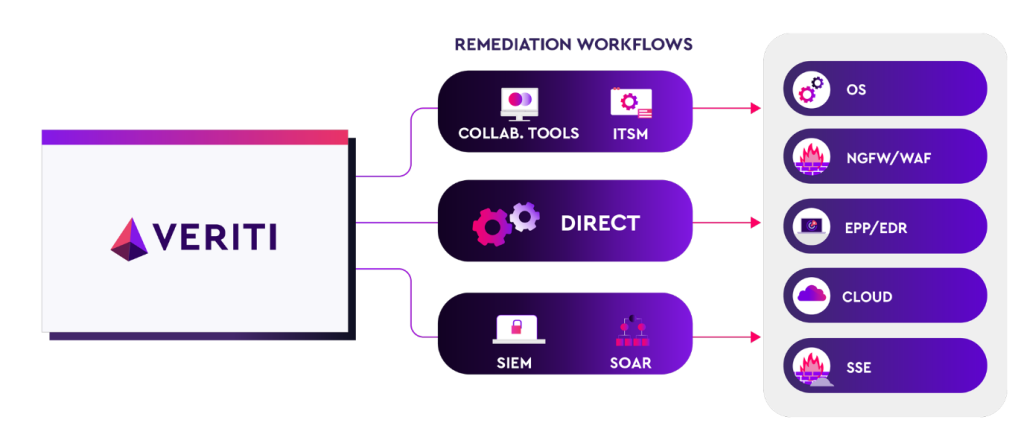
Veriti’s modern approach to improving security posture involves continuous automated assessment and optimization of security controls. Our solution provides bidirectional integrations with network security, endpoint security, vulnerability assessment, and other security tools. This enables cross-control configuration, event, and telemetry analysis, helping identify protection gaps or sources of false positive alerts.
Veriti leverages the same APIs used to fetch all configurations to apply actual remediation guidelines. This involves implementing compensating controls from the OS-level (changing registries on endpoints) to the cloud (SSE and CNAPP/CWPP tools). This comprehensive approach ensures that organizations can:
Swiftly Remediate Vulnerabilities:
By automating the entire lifecycle, from exposure identification and prioritization to evaluation and secure remediation.
Enhance Security Posture:
By closing exposure gaps and triggering surgical compensating controls for immediate efficacy.
Maintain Operational Continuity:
By predicting the ripple effects of any remediation action, ensuring that business operations remain uninterrupted.
As organizations strive to enhance their security posture, they often face challenges such as too many security tools, misconfigured controls, and the complexities of taking remediation actions. Compensating controls provide a viable solution to these challenges, ensuring proactive security, managing risks, and maintaining operational continuity. By leveraging automation and advanced threat intelligence, Veriti helps organizations move from seeking impossible certainty to actually remediating, mitigating, and sharing intelligence. This ensures that each step forward counts, integrating all tools at their disposal and mobilizing remediation efforts across security teams and tools.




