As the buzz around Meta’s new text-based social networking app, Threads, continues to grow, attackers are seizing the opportunity to take advantage of the buzz. In recent weeks, we have observed a surge in the creation of suspicious domains, with over 700 domains related to Threads being registered daily. These domains pose a significant risk as they can be used to deceive users, distribute malware, and lure unsuspecting individuals into downloading untrusted versions of the app. In this research blog, we shed light on this emerging threat and provide examples of suspicious domains to raise awareness and promote vigilance.
THE RISING THREAT
Among the newly registered domains, there are several that exhibit suspicious characteristics and potential malicious intent. One such example is “Threadsapk[.]download,” a potential phishing domain created just a few days ago. This domain raises concerns as attackers may use it to trick users into sharing sensitive information or credentials.

Another concerning domain is “Threadsappz[.]com” which offers an Android version of the app for download. However, users should exercise caution, as this download is not sourced from the official app store or Google Play. Instead, it redirects to an external source, in this case, a Google Drive, where the APK file can be downloaded. Such downloads from untrusted sources can pose significant security risks, including the potential for malware infection.
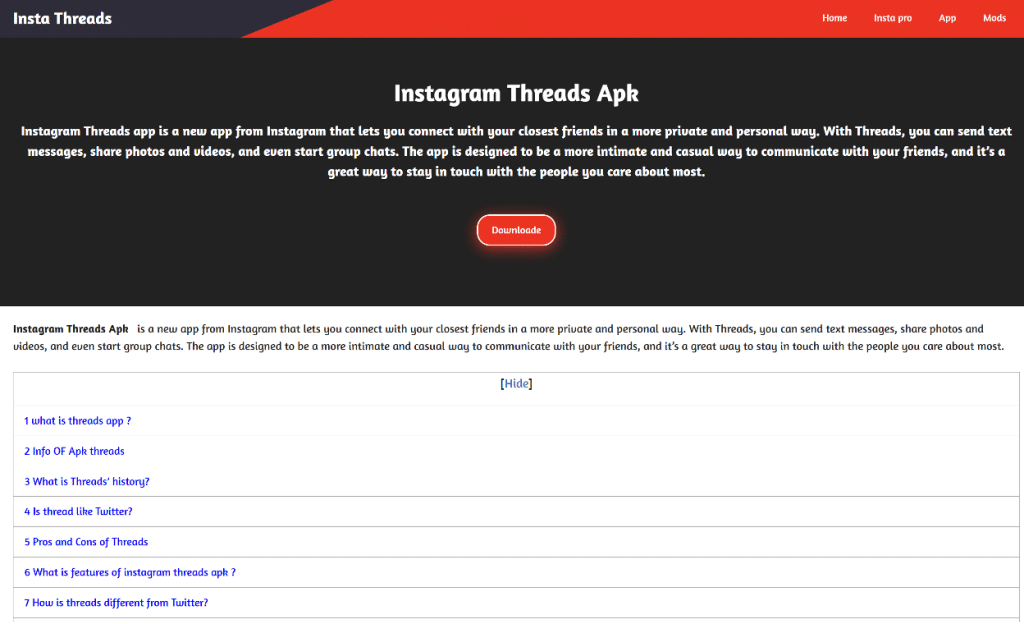
This is similar to the previous story, but in this instance, the file can be downloaded from MediaFire instead of the app stores.

LIST OF SUSPICIOUS DOMAINS
We have compiled a list of domain lookalikes that were registered just yesterday. These domains mimic the legitimate Threads app or use variations in their names to mislead users. By sharing this list, we aim to create awareness and prevent unsuspecting individuals from falling victim to these deceptive tactics. Please refer to the attached list for further details on these suspicious domains.
| threads[.]ovh |
| whatisthreads[.]com |
| socialthreads[.]store |
| threadsapk[.]download |
| threadsfollower[.]org |
| threadsmeme[.]com |
| bestofthreads[.]com |
| threadsapp[.]dev |
| metathreads[.]social |
| threadsexpert[.]com |
| threads-apk[.]org |
| metathreads[.]website |
| threadsapp[.]shop |
| threadspix[.]com |
| tthreadsfollowers[.]com |
| threadsl[.]com |
| threadsinstagram[.]app |
And many more..
STAYING VIGILANT
It is crucial for users to exercise caution and follow best security practices. To protect yourself from potential threats related to the Threads app:
- Download from trusted sources: Only download the Threads app from official app stores, such as the Apple App Store or Google Play Store, to ensure you are accessing the genuine version.
- Be cautious of suspicious links: Avoid clicking on links shared through unverified sources, emails, or unfamiliar websites, as they may lead to malicious websites or downloads.
- Verify domain authenticity: Pay close attention to the domain name of any Threads-related websites you visit. Be wary of domains that have spelling variations or lookalikes designed to deceive users.
- Keep software up to date: Regularly update your device’s operating system and apps to ensure you have the latest security patches and protections against known vulnerabilities.
As the popularity of Meta’s Threads app continues to rise, attackers are capitalizing on the excitement to carry out malicious activities. By creating a large number of suspicious domains, they aim to deceive users and distribute malware. It is crucial for users to remain vigilant, download apps only from trusted sources, and be cautious of suspicious links.




